What is Bring Your Own Device and How to Create Your BYOD Policy Today
A lot has changed in the workplace since there were strict rules against employees using their personal devices to handle company data. Competent managers and business owners have recognized the advantages of allowing team members to perform office tasks with their own smartphones or computers. However, some risks come with allowing external devices onto your organization’s network, and you need a Bring Your Own Device (BYOD) policy to reduce the likelihood of these risks crippling your organization.
What is BYOD (Bring Your Own Device)?
Within the workplace context, BYOD refers to employees making use of their preferred personal devices to perform work-related tasks and other official duties. These devices can range from laptops to smartphones or even desktop PCs for those who work from home.
A VoIP service provider called BroadVoice is credited as the first company to use BYOB in the corporate world. In 2004, they used it to launch a service that allowed users to send business calls to personal mobile devices. Around this time, the proliferation of increasingly powerful yet affordable computing devices meant that a lot more people had access to equipment that was just as powerful as the ones assigned to them at work. Mobile phones became smartphones that allowed you to work effectively on the go, and tablet computers escalated things further.
As more businesses adopted cloud computing trends for increased efficiency, it made sense for business owners and managers to encourage the use of employee-owned devices. A program like this helped improve enterprise mobility while keeping costs relatively low. But that was just the beginning of why BYOD became so attractive to modern businesses.

Four Reasons Why BYOD is Important
As the Bring Your Own Device trend began to spread and more companies implemented policies supporting it, the advantages of BYOD over the traditional IT systems of the time became apparent.
- Reduced Costs: Businesses are always looking for ways to minimize their expenditure. Not having to purchase or maintain physical computing hardware for every employee can be a great way to do just that. According to a 2016 Cisco report, companies with a BYOD policy save $350 per employee on average.
- Flexibility: BYOD enhances mobility, and with that comes the ability to work from almost anywhere, enhancing flexibility for the growing remote workforce.
- Increased Productivity: The convenience and familiarity of using a personal device can lead to greater effectiveness at work. Research by Samsung has shown that employees gained about an hour of work time by incorporating their smartphones into their workflow. That’s a productivity boost of 34 percent.
- Employee Satisfaction: Allowing employees to use the same devices for work and their personal lives will improve their work-life balance and lead to a happier, more productive workforce.
Three Risks of BYOD
The benefits of BYOD make it an attractive policy direction, but there arerisks of BYOD to consider before deciding to go this route.
- Data Breaches & Cyberattacks: There is an increased security risk involved in allowing employees to use their own devices for work. Most of this risk is because they are less likely to have the cybersecurity solutions required for the workplace on their devices. Also, physical security (where devices are used outside of the workplace) may be lax, leaving confidential company data vulnerable to unauthorized persons.
- Complicated IT Management: Managing an organization’s IT infrastructure is challenging even with equipment specifically chosen and optimized for operational efficiency. It becomes even more challenging when everyone brings their laptops and mobile devices, each with its unique configurations and quirks. Integrating all these devices and ensuring that their users can access the resources they need to function effectively is no small task.
- Privacy Issues: Some employees who want to keep their work and personal lives separate may view using their personal computers for work as an invasion of their privacy, especially when installing security software on their devices.
These identified risks are why a Bring Your Own Device Policy is necessary for any organization looking to reap the benefits of allowing personal devices in the workplace.
What is a Bring Your Own Device Policy?
A BYOD policy is a set of guidelines put in place by a company to manage the use of personal devices for work-related activities. The policy specifies the requirements that these devices and their owners must meet and the cybersecurity measures the organization must enforce for a safe and effective BYOD program.
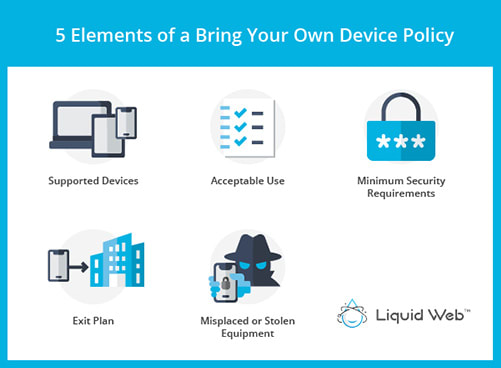
Five Elements of a Bring Your Own Device Policy
An effective BYOD policy should contain the following sections:
- Supported Devices: Your BYOD policy should define what devices will be acceptable for employees to use for work. There should be details on minimum hardware specifications, operating systems, and communication modes that the device supports. It would help if you also considered what devices employees already have when drafting this policy section.
- Acceptable Use: This section outlines the requirement that must be met by your staff while using their personal devices to access the company networks and infrastructure to prevent the misuse of company resources. Also covered here will be procedures for keeping company data separate from personal data and privacy guidelines.
- Minimum Security Requirements: Password policies, antivirus software, physical security recommendations, and other security solutions are defined in this section. The purpose of these requirements is to reduce the risk of a security breach from any personal devices accessing your company’s IT systems. The guidelines in this section would also ensure compliance with industry and state legislations for data security.
- Exit Plan: This covers the steps to retrieve and secure corporate data stored on an employee’s computer or smartphone when an employee leaves the organization. Ensure your team covers any business data challenges here as well.
- Misplaced or Stolen Equipment: For devices that get lost, your BYOD policy should have a section that takes care of managing these types of scenarios. This part of your policy should include steps for tracking these stolen devices, locking them to prevent access, as well as remote wiping the storage to prevent access to sensitive data.
Five Questions to Ask When Creating Your Bring Your Own Device Policy
Is BYOD Right for Your Organization?
Several factors can affect your decision to implement a BYOD policy for your organization. Ask yourself the following:
- How big is your team?
- What kind of personal devices do they use?
- Can your IT team effectively manage a BYOD program?
- What type of data does your organization deal with?
- Are there legal requirements that may be difficult to meet with a BYOD program?
These questions will help you decide if implementing a BYOD policy is a good idea - or not.
What is the Scope of Your BYOD Program?
Will you allow all employees to work with their devices, or will it only be teams from specific departments? This decision will largely depend on the job description of each unit and the type of data they work with.
For instance, your design team may have specialized personal devices that make them more efficient at their job and would benefit from being allowed to continue using them.
On the other hand, the management team might experience a change in their performance if they are a part of your BYOD program.
How Will You Manage Personal Devices?
The success of your BYOD program is dependent on how you manage these devices. Picking the right mobile device management software and other remote monitoring tools can help your IT team easily track how personal devices will be used in your organization.
Who Pays for What?
How will you separate expenses that are work-related from those that aren’t?
Staff will always have expenses when they use personal devices for official purposes. These expenses include Internet data plans, repair costs, software subscriptions, and more.
What Alternatives are Available?
Not all employees will have devices that meet the requirements of your BYOD policy, so your policy should consider what to do in this scenario. For example, do you pay for the employee to purchase better equipment or provide items from the office supply?
Getting Your BYOD Program Off the Ground
A BYOD program is a great way for small businesses to drive their growth while keeping IT infrastructure costs low. However, since these personal devices may be processing sensitive data within your IT systems, you cannot ignore the risks involved.

Marho Atumu
Marho is a Community Support agent at The Events Calendar and enjoys helping people discover how information technology can provide great solutions to their everyday problems. His career in IT can clearly be traced to his love for all things science fiction.
Keep up to date with the latest Hosting news.



